enable. protect. everywhere.
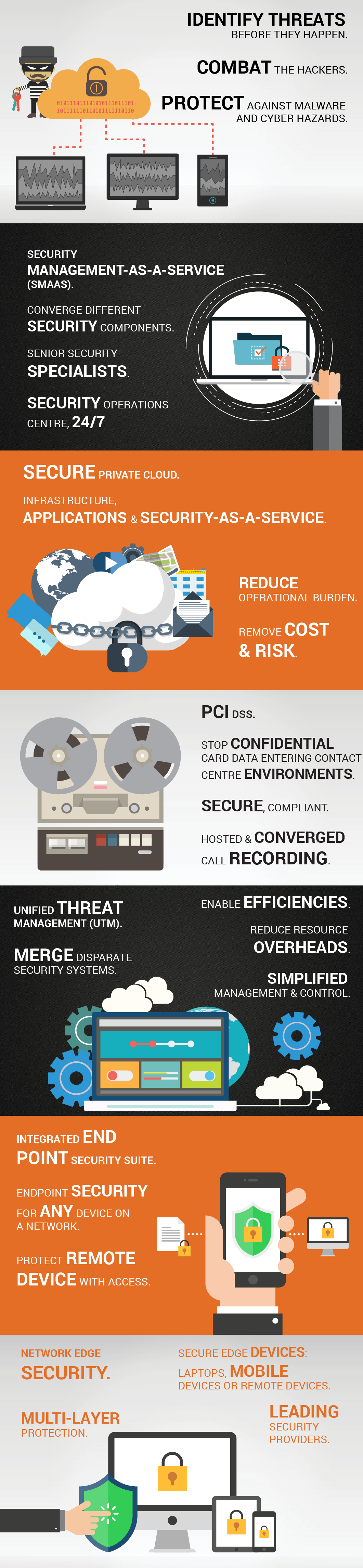
Cybercrime in this truly digital era is not only on the increase, but a daily reality for most of the world’s multinational corporations. Threats to data integrity exist both inside and outside organisations, making it increasingly more difficult to detect and contain without the right security solutions.
Borwood’s security solutions have a multi-layered design as we integrate leading vendors to deliver comprehensive protection and compliance. Our solutions identify threats before they negatively impact your business, allowing you to focus on service delivery and client satisfaction, while we combat the hackers.
Security Management as a Service
________________________________________________________
Security Management as a Service is a state-of-the-art security solution that ties in various security components to ensure maximum risk protection.
Among the top uses for SMaaS, are activity monitoring, high-risk resource profiling, weekend and off-hours activity, high-risk user analysis and advanced correlation. It can also play an important role in predictive modelling, user activity certification, peer group analysis and integration with ticketing systems.
Borwood’s SMaaS solutions offers continuous distributed denial-of-service attack management, resistance and mitigation. Our 24/7 security operations centre is staffed by senior specialists.
Borwood takes the “listen, think and deliver” approach to security, starting with an analysis of the current systems, then by looking at ways in which the customer could be compromised going forward. By understanding the gaps, we are able to deliver a solution that fully future-proofs your business against cybercrime.
PCI DSS Compliant Platform
The PCI-DSS (Payment Card Industry Data Security Standard) is an information security standard for organisations that process and/or keep card payment data from major card schemes around the world.
Borwood’s PCI DSS compliance services stops any card data from entering the contact centre environment. It further removes existing card data from the system and delivers secure, compliant, hosted converged call recording.
At Borwood, we use regularly updated anti-virus software and encrypt transmission of data across open and public networks. Access to cardholder data can be restricted by the customer and is kept on a need-to-know basis.
“There are two ways to achieve compliance to PCI DSS” says Borwood’s Steve Maxwell.
“You can either prevent card data from entering your environment, or you can ensure you do not have any Cardholder Data Environments (CDEs)”
“Our single integration SaaS platform provides PCI compliance for agent-managed phone payments, IVR Assist automated phone payments, secure call recording archive in the cloud, as well as call recording for FCA and Dodd Frank legislation.”
Integrated End Point Security Suite
End point security refers to a protection methodology applied to any device on a network, or remote devices with access to a network. Laptops, mobile phones or other wireless devices on a network create potential entries for a host of threats and need to be secured at all times.
Borwood’s end point security suite uses the latest solutions and technology in the development, implementation and management of your endpoint strategy. It minimises threats, operational interruptions, as well as the potential legal implications and costs associated with lost or stolen data.
Borwood delivers a combination of multi-layered threat protection ensuring that all vulnerabilities are covered, stopping data leaks before they occur and giving you peace of mind.
Secure Private Cloud
A managed secure private cloud solution removes cost, risk and operational burden. The integration of cloud computing into a private network means that your managed cloud solution is not on the public internet, making the environment an extension of your network. This reduces the need to add infrastructure or to employ staff specifically to manage the space.
Borwood’s Private Secure Cloud provides infrastructure, applications and security as part of our service. Authentication, anti-malware, intrusion detection, and many other services form part of our applications.
One of the key benefits of a managed private cloud solution is the speed of service evolution, increased customisation and reliability – it’s about agility as opposed to a straightforward case of OPEX versus CAPEX.
Borwood excels in this private, secure cloud space. With the acquisition of a secure private cloud company in Singapore, we have bulked up our global skill set to deliver unparalleled experience and compliance.

Unified Threat Management (UTM)
Ideal for businesses and enterprises with a distributed workforce and remote networks, UTM (Unified Threat Management) brings disparate security systems together so that they can be managed from a single point. This enables efficiency and reduces the resource overhead, while allowing complete visibility of the organisation’s firewalls, anti-virus, VPN, DLP, intrusion-prevention and reporting.
Borwood maintains highly secure connections via a secure VPN and implements customised rules to meet your business’ specific needs. Our solution identifies and deflects internet-based attacks to the private network or through the internet connection. We combine the industry’s top Unified Threat Management platforms with multi-threat security systems to provide a truly secure solution for your business.
Full integration with our MPLS IP-VPN solutions creates a complete networking and managed security solution for all the locations across the globe.
Network Edge Security
The edge is where data flows in and out of your network through laptops, mobile devices or remote devices with access to the network.
Edge devices need to be more secure than “core devices” as it is at this point where access to the outside world leaves vulnerabilities. It is critical to choose the right technologies and partners to secure your network.
We implement Multi-Layer protection utilising best-of-breed applications from leading security providers.
Borwood’s team of security specialists understand the different layers of protection, applying solutions and logic to construct a wall that your clients and staff can rely on.
Solutions
Networking
MPLS IP-VPN Services
Software Defined Networking
Private Circuit Network
Dedicated Internet Access (DIA)
Network Security
Customer Experience (CX)
Hosted Telephony
Session Initiated Protocol (SIP) Trunking
Call origination and Termination
Contact Centre-as-a-Service (CCaaS)
Cloud
Hosted Security as a Service (SECaaS)
Business Continuity and Disaster Recovery Planning
Unified Email Management (UEM)
Security
PCI DSS Compliant Platform
Integrated Endpoint Security Suite
Secure Private Cloud
Unified Threat Management (UTM)
Company
Call us
South Africa +27 876 130000
United Kingdom +44 207 743 7500
Australia +61 28 015 7612
Singapore +65 3157 3609
Mauritius +230 5254 5478